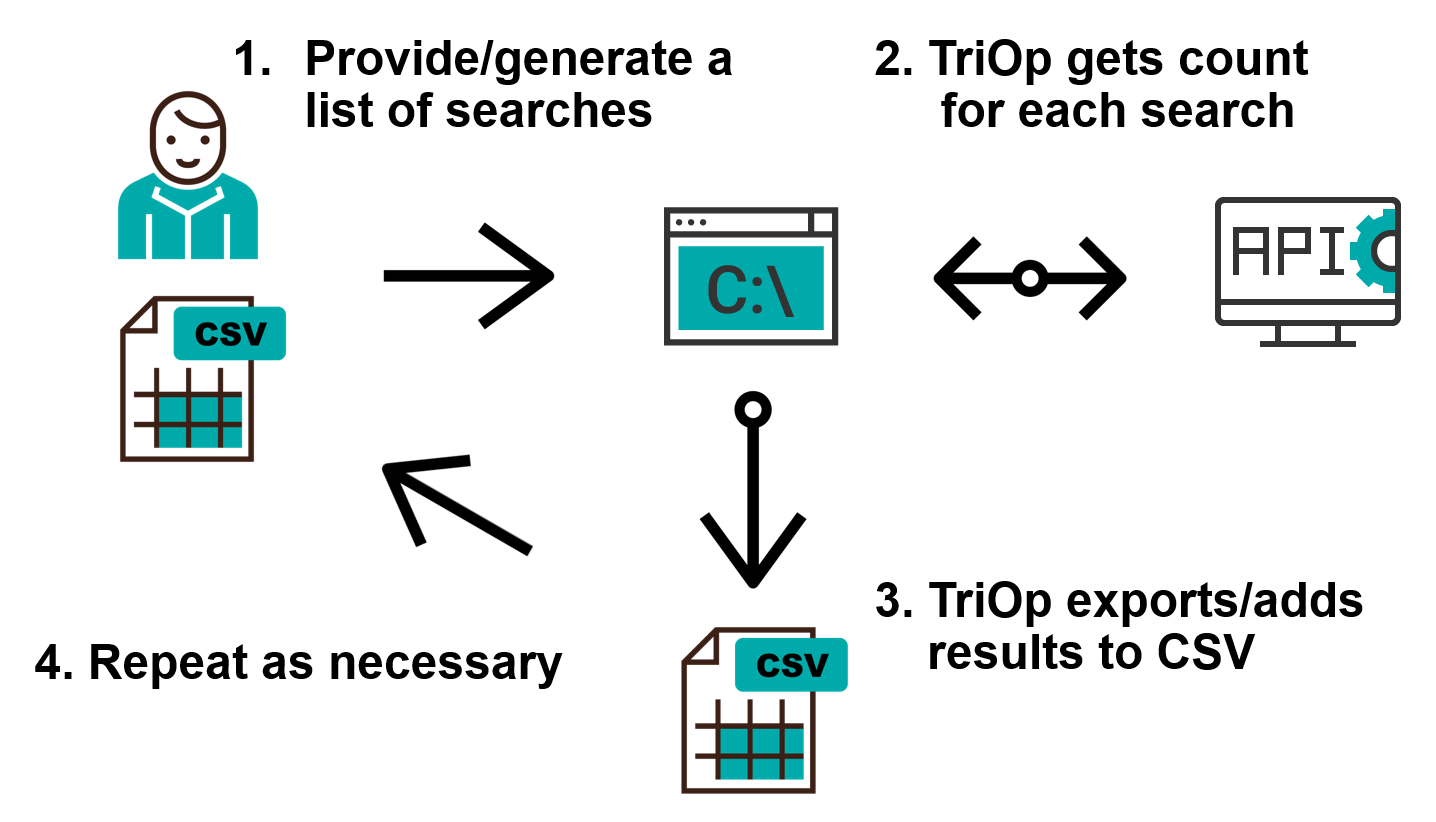
Shodan-based vulnerability assessment tool modular architecture. CPE,... | Download Scientific Diagram
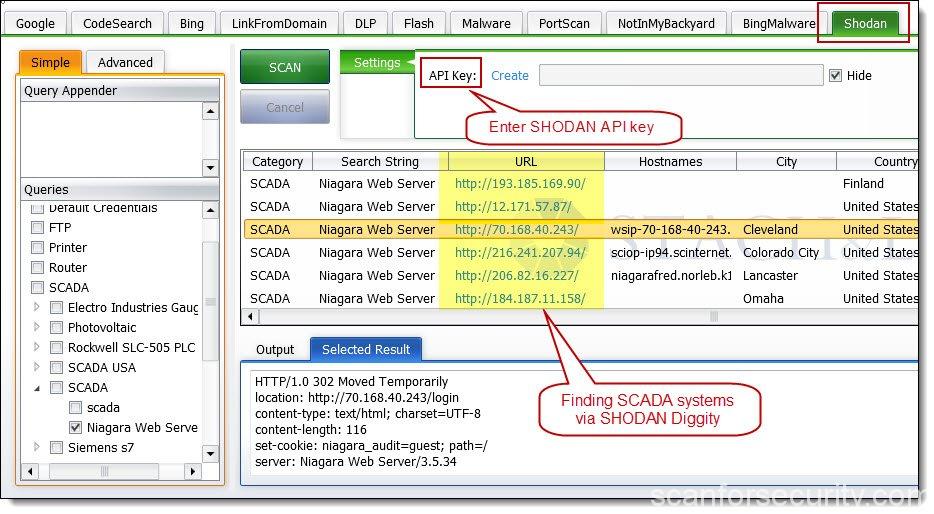
Shodan-Eye - Tool That Collects All The Information About All Devices Directly Connected To The Internet Using The Specified Keywords That You Enter
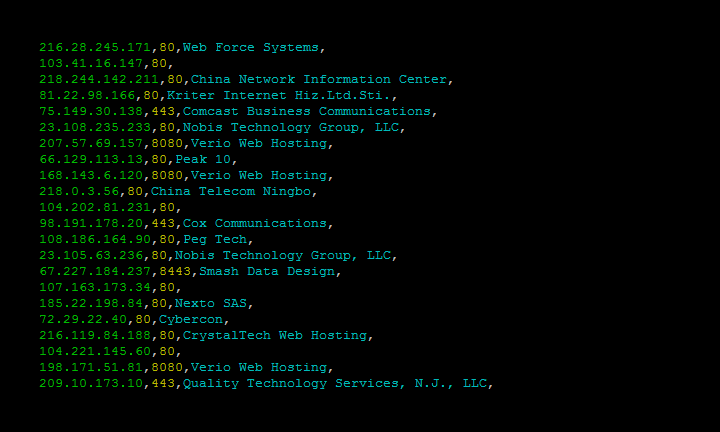
Shodan on X: "Introducing nrich: a tool to quickly find the open ports and vulnerabilities for a list of IPs - https://t.co/Y5raA1YO30 https://t.co/H5gs74hAUD" / X

Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
GitHub - BullsEye0/shodan-eye: Shodan Eye This tool collects all the information about all devices directly connected to the internet using the specified keywords that you enter. Author: Jolanda de Koff