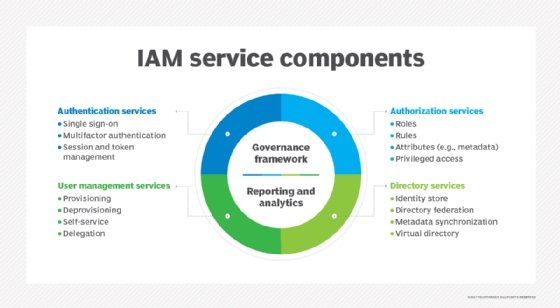
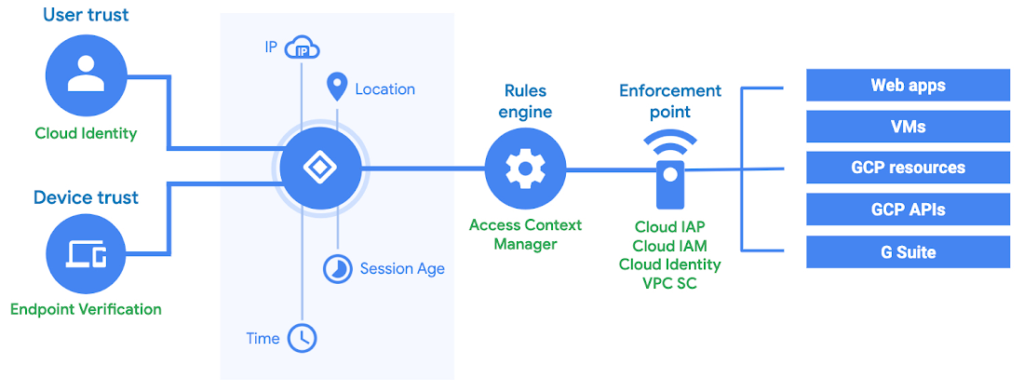
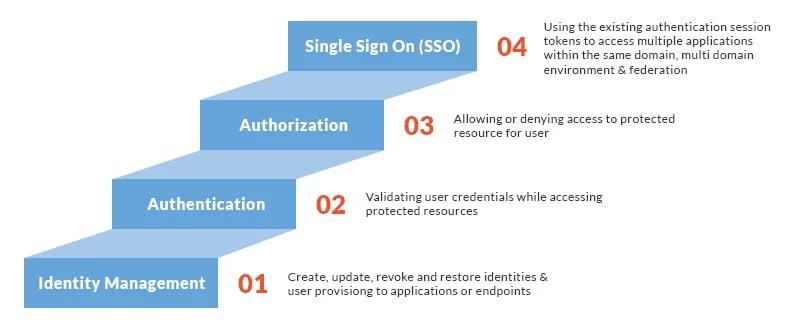
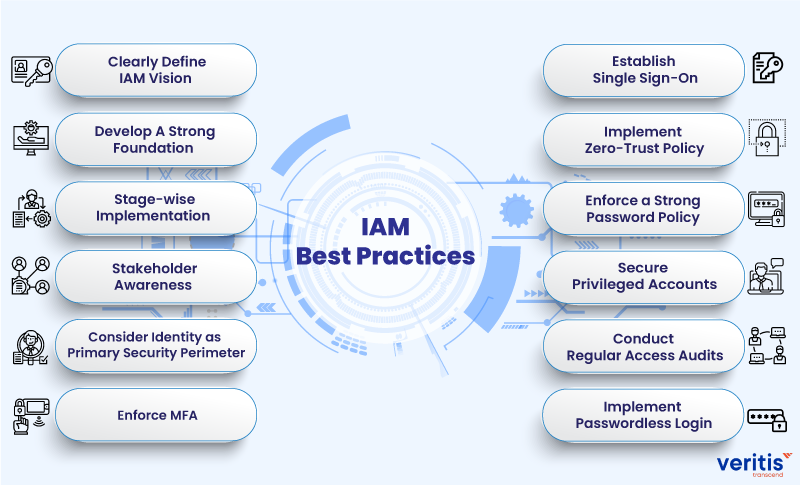
Explore the two critical cybersecurity tools: Identity and Access Management (IAM) and Privileged Access Management (PAM). Which solution aligns with your organization's security strategy? Join the conversation and share your insights! :

Analyse de la taille et de la part du marché des services de sécurité IAM - Rapport de recherche de lindustrie - Tendances de croissance
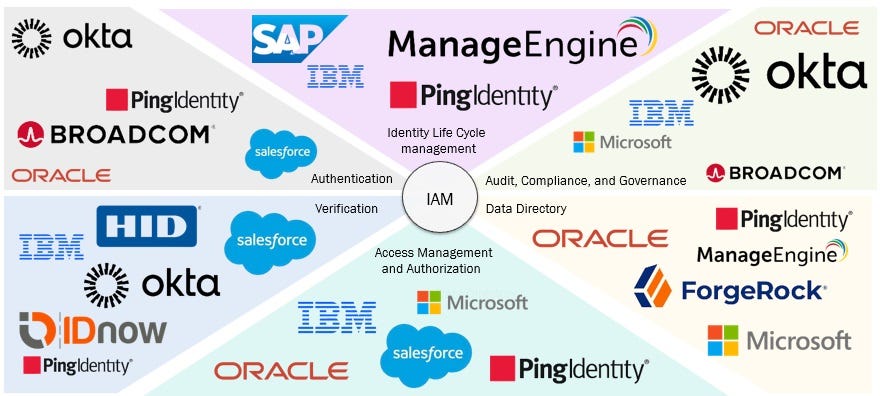
A Journey into the Realm of IAM: An Introduction to the Cutting-Edge Solutions in the Market | by Hilda Machando | Medium