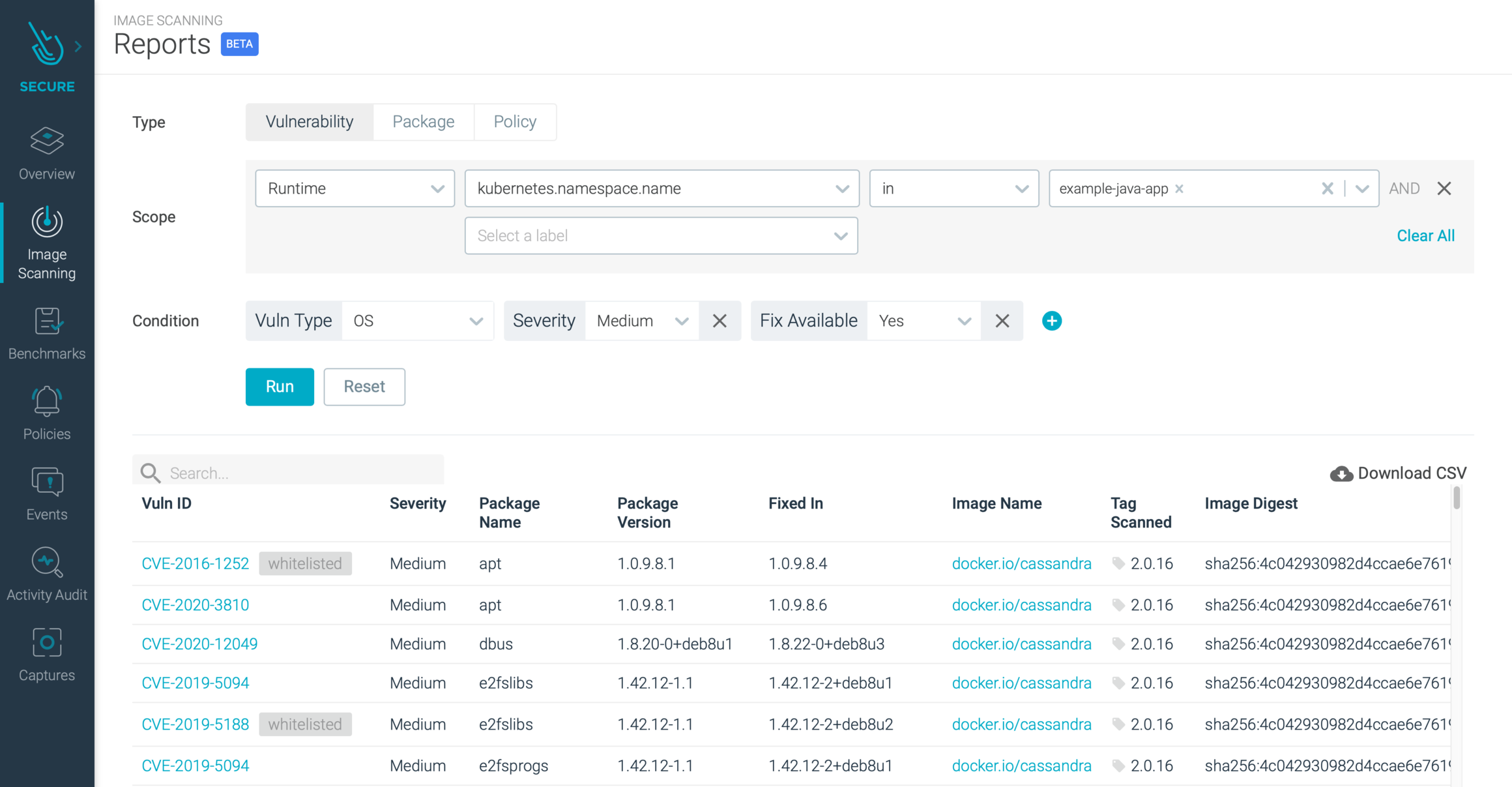
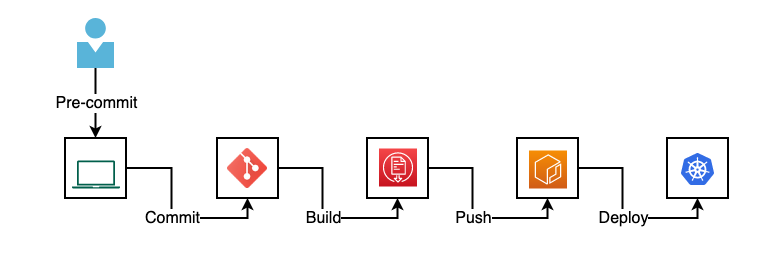
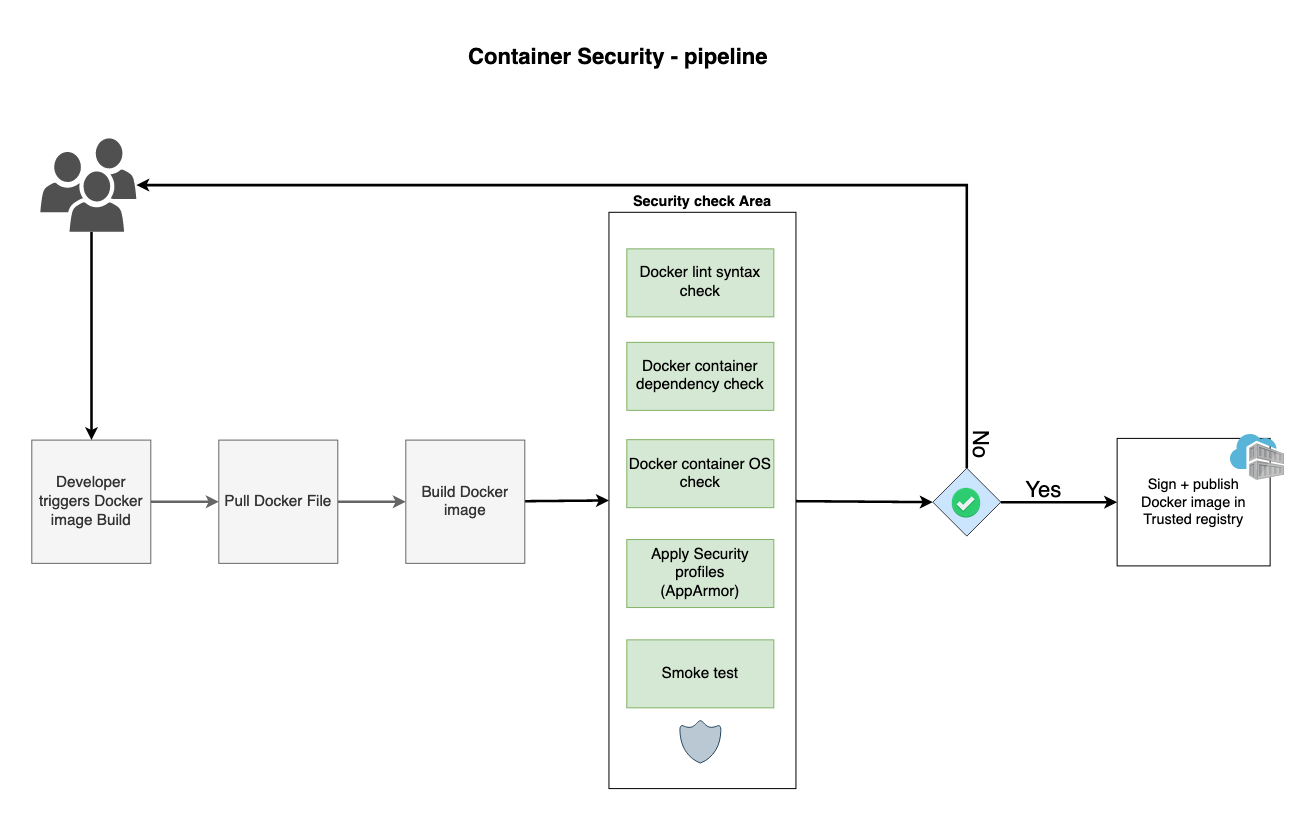
Patch Container Images for vulnerabilities, ft. Microsoft's Copacetic. | by Raghavendra Mallela | Jan, 2024 | Medium

Announcing third-party code scanning tools: infrastructure as code and container scanning - The GitHub Blog
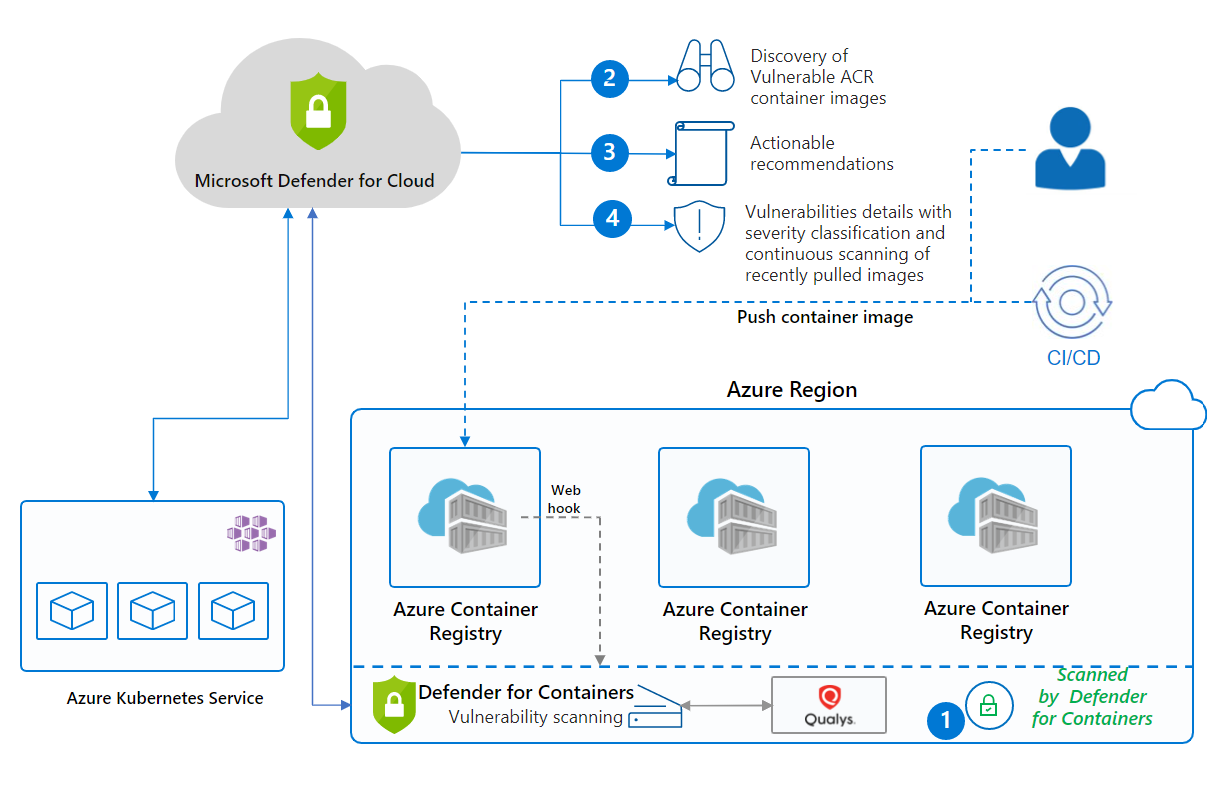
Enhance your CI/CD deployment by using Vulnerability Assessments from Microsoft Defender for ACR - Microsoft Community Hub

Docker Vulnerability Scanning Tools: Free, Open-Source, and Paid Options for Secure Container Images | by Hinanaseer | Medium