Hackind_tech on Instagram: "⚠️Diving into the world of Bluetooth security: ever heard of bluebugging, bluesnarfing, BTCrack, and Btlejack📱📡🔒🔥 Exploring the intricacies of digital landscapes and staying curious. 🔍💡 👉 Bluing:This term is

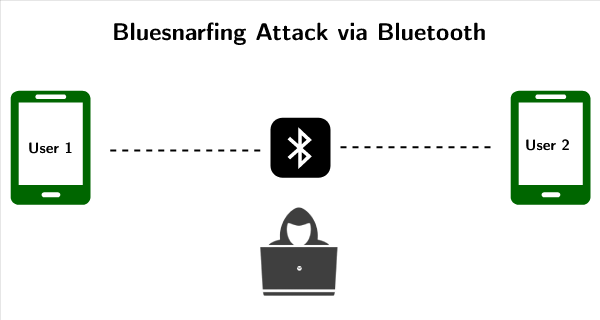
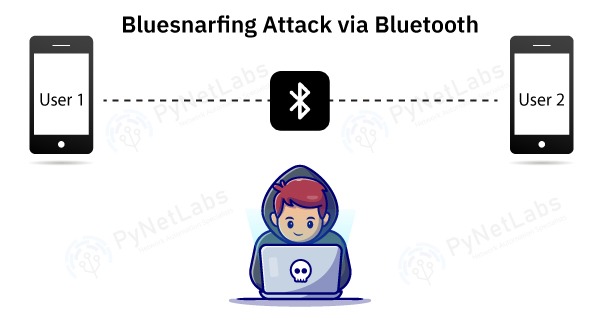
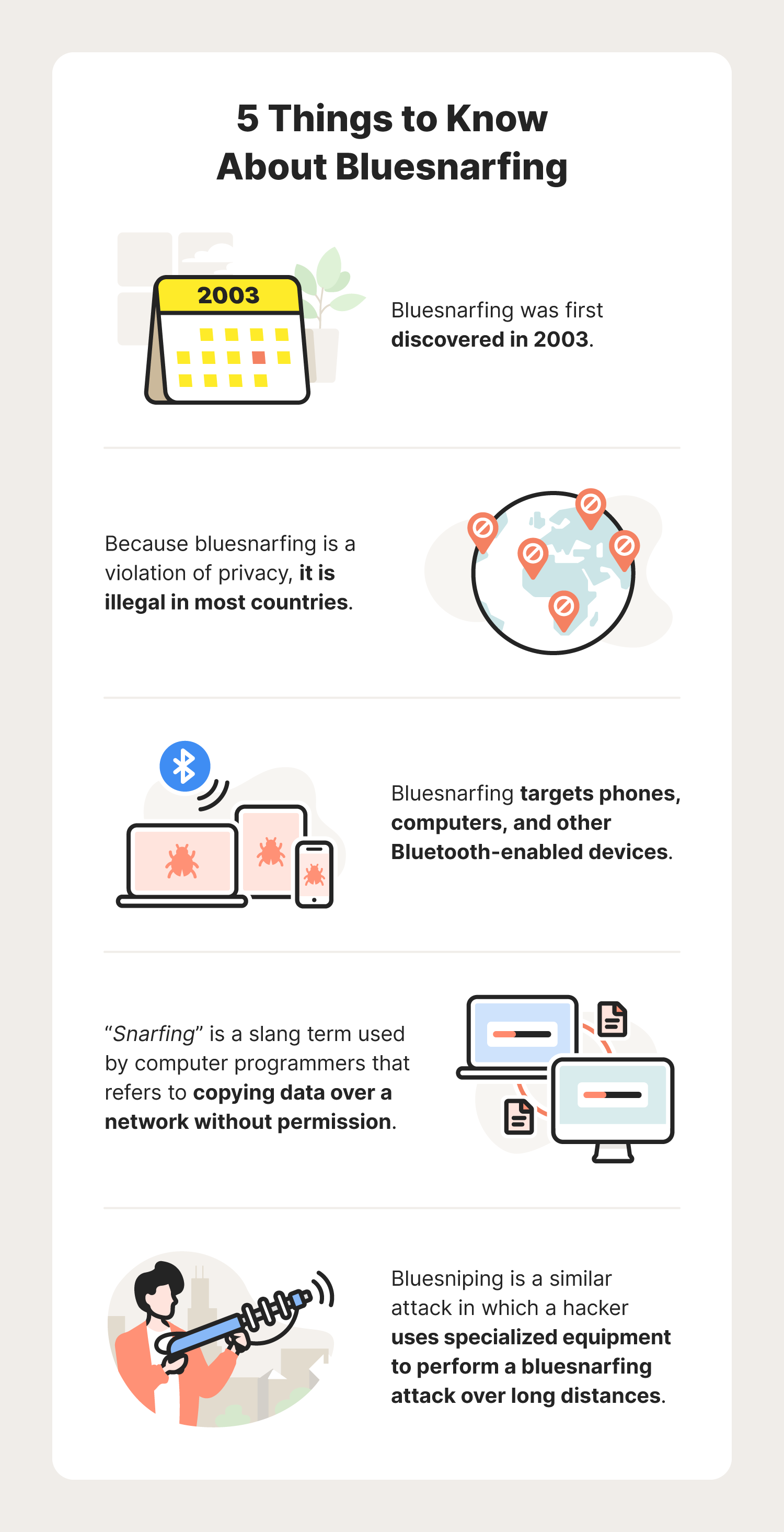
Bluesnarfing, Sybil Attacks and Other Emerging Cybercrime Tactics Bluesnarfing, Sybil Attacks and Other Emerging Cybercrime Tactics

Cybersecurity by CyberKid - 🌀Bluetooth Attacks 🔹Blueprinting 🔹Bluesnarfing 🔹Bluebugging 🔹Bluejacking 🔹Bluesmack 🔖#infosec #cybersecurity #hacking #pentesting #security 👤facebook.com/Cyberkid1987 👤x.com/Anastasis_king 👤bsky.app/profile ...

Hackind_tech on Instagram: "⚠️Diving into the world of Bluetooth security: ever heard of bluebugging, bluesnarfing, BTCrack, and Btlejack📱📡🔒🔥 Exploring the intricacies of digital landscapes and staying curious. 🔍💡 👉 Bluing:This term is


)